This PowerShell script will create a report of users that are members of the following privileged groups:
- Enterprise Admins
- Schema Admins
- Domain Admins
- Cert Publishers
- Administrators
- Account Operators
- Server Operators
- Backup Operators
- Print Operators
This is the default list of privileged groups I’ve set, but you can adjust the privileged groups directly within the getForestPrivGroups function if needed.
The original script was written by Doug Symalla from Microsoft and posted onto the TechNet Script Center: List Membership In Privileged Groups
This was accompanied by two TechNet Blogs:
- Audit Membership in Privileged Active Directory Groups. A Second Look.
- Too Many Admins in Your Domain: Expose the Problem(s) and Find a Solution. (Don’t forget PowerShell)
The script was okay, but needed several updates to be more accurate and bug free. As Doug had not published an update since 26th April 2013, I though that I would. The changes I made are documented in the script.
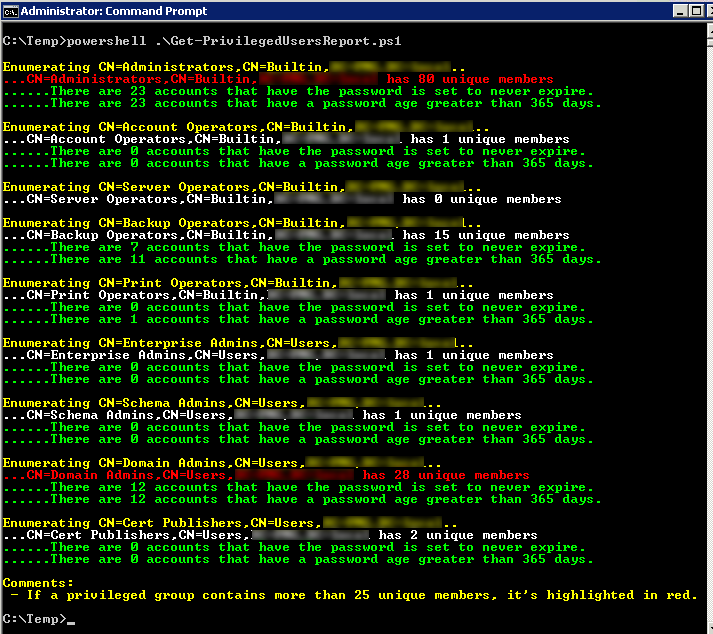
The following screen shot is the output from a recent Active Directory Health Check I completed:
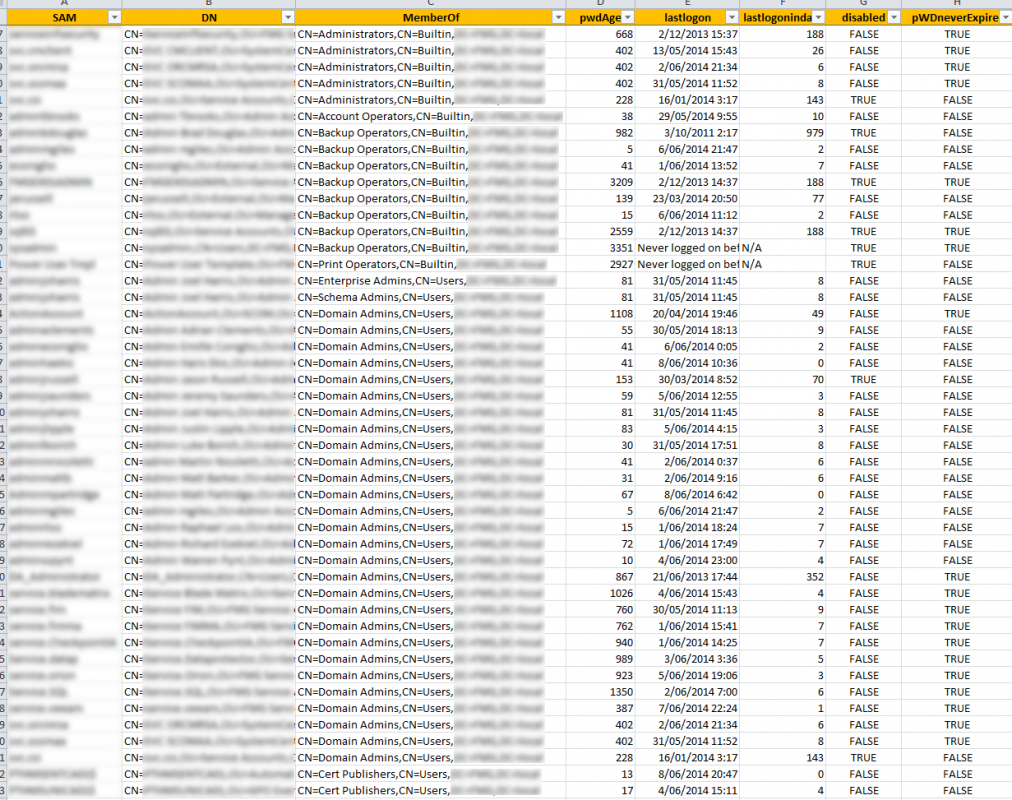
The following screen shot is a snippet of the detailed output that it writes to a CSV file. An explanation of the columns is:
- SamAccountName = The SamAccountName of the user.
- DistinguishedName = The DistinguishedName of the user.
- MemberOf = The DistinguishedName of the privileged group the user is a member of.
- PasswordAge = The password age.
- LastLogon = Last Logon Time Stamp. Helps to decide if it’s still in use/current.
- LastLogonInDays = Current date – Last Logon Time Stamp. Also helps to decide if it’s still in use/current.
- Disabled = Is the account disabled? Helps to decide if it can be removed from the group.
- PasswordNeverExpires = Is the password set to never expire?
- AccountExpires = When does or did the account expire, or is it set to never expire?
- Description = Not visible in this screen shot. But this column is the description of the account as set in Active Directory. This helps explain its usage, if not obvious.
- Notes = Not visible in this screen shot. But this column contains any notes made about the account as set in Active Directory. This also helps explain its usage, if not obvious.
IMPORTANT: From the output you’ll notice that there are a lot of user accounts in the Built-In Administrators group. This can be alarming at first pass, but important to understand that by default the Domain Admins group is a member of the Built-In Administrators group. Therefore, users in the Domain Admins group will also appear as a user of the Built-In Administrators group in this report. Likewise, by default the Enterprise Admins group is also a member of the Built-In Administrators group. My advice is to not focus on the Built-In Administrators group first. But rather reduce your Domain Admins and Enterprise Admins, which in turn will clear up the Built-In Administrators group too.
Here is the Get-PrivilegedUsersReport.ps1 script:
001 002 003 004 005 006 007 008 009 010 011 012 013 014 015 016 017 018 019 020 021 022 023 024 025 026 027 028 029 030 031 032 033 034 035 036 037 038 039 040 041 042 043 044 045 046 047 048 049 050 051 052 053 054 055 056 057 058 059 060 061 062 063 064 065 066 067 068 069 070 071 072 073 074 075 076 077 078 079 080 081 082 083 084 085 086 087 088 089 090 091 092 093 094 095 096 097 098 099 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 | <# This script will create a report of users that are members of the following privileged groups: - Enterprise Admins - Schema Admins - Domain Admins - Cert Publishers - Administrators - Account Operators - Server Operators - Backup Operators - Print Operators A summary report is output to the console, whilst a full report is exported to a CSV file. The original script was written by Doug Symalla from Microsoft: - http://blogs.technet.com/b/askpfeplat/archive/2013/04/08/audit-membership-in-privileged-active-directory-groups-a-second-look.aspx - http://gallery.technet.microsoft.com/scriptcenter/List-Membership-In-bff89703 The script was okay, but needed some updates to be more accurate and bug free. As Doug had not updated it since 26th April 2013, I though that I would. The changes I made are: 1. Addressed a bug with the member count in the main section. Changed... $numberofUnique = $uniqueMembers.count To... $numberofUnique = ($uniqueMembers | measure-object).count 2. Addressed a bug with the $colOfMembersExpanded variable in the getMemberExpanded function Added... $colOfMembersExpanded=@() 3. Enhanced the main section 4. Enhanced the getForestPrivGroups function 5. Enhanced the getUserAccountAttribs function 6. Added script variables 7. Added the accountExpires and info attributes 8. Enhanced description of object members (AKA csv headers) so that it's easier to read. Script Name: Get-PrivilegedUsersReport.ps1 Release 1.2 Modified by Jeremy@jhouseconsulting.com 13/06/2014#>#-------------------------------------------------------------# Set this to maximum number of unique members threshold$MaxUniqueMembers = 25# Set this to maximum password age threshold$MaxPasswordAge = 365# Set this to true to privide a detailed output to the console$DetailedConsoleOutput = $False#-------------------------------------------------------------################## Function to Expand Group Membership ################function getMemberExpanded{ param ($dn) $colOfMembersExpanded=@() $adobject = [adsi]"LDAP://$dn" $colMembers = $adobject.properties.item("member") Foreach ($objMember in $colMembers) { $objMembermod = $objMember.replace("/","\/") $objAD = [adsi]"LDAP://$objmembermod" $attObjClass = $objAD.properties.item("objectClass") if ($attObjClass -eq "group") { getmemberexpanded $objMember } else { $colOfMembersExpanded += $objMember } }$colOfMembersExpanded} ########################### Function to Calculate Password Age ##############Function getUserAccountAttribs{ param($objADUser,$parentGroup) $objADUser = $objADUser.replace("/","\/") $adsientry=new-object directoryservices.directoryentry("LDAP://$objADUser") $adsisearcher=new-object directoryservices.directorysearcher($adsientry) $adsisearcher.pagesize=1000 $adsisearcher.searchscope="base" $colUsers=$adsisearcher.findall() foreach($objuser in $colUsers) { $dn = $objuser.properties.item("distinguishedname") $sam = $objuser.properties.item("samaccountname") $attObjClass = $objuser.properties.item("objectClass") If ($attObjClass -eq "user") { $description = $objuser.properties.item("description")[0] $notes = $objuser.properties.item("info")[0] If (($objuser.properties.item("lastlogontimestamp") | Measure-Object).Count -gt 0) { $lastlogontimestamp = $objuser.properties.item("lastlogontimestamp")[0] $lastLogon = [System.DateTime]::FromFileTime($lastlogontimestamp) $lastLogonInDays = ((Get-Date) - $lastLogon).Days if ($lastLogon -match "1/01/1601") { $lastLogon = "Never logged on before" $lastLogonInDays = "N/A" } } else { $lastLogon = "Never logged on before" $lastLogonInDays = "N/A" } $accountexpiration = $objuser.properties.item("accountexpires")[0] If (($accountexpiration -eq 0) -OR ($accountexpiration -gt [DateTime]::MaxValue.Ticks)) { $accountexpires = "<Never>" } else { $accountexpires = [datetime]::fromfiletime([int64]::parse($accountexpiration)) } $pwdLastSet=$objuser.properties.item("pwdLastSet") if ($pwdLastSet -gt 0) { $pwdLastSet = [datetime]::fromfiletime([int64]::parse($pwdLastSet)) $PasswordAge = ((get-date) - $pwdLastSet).days } Else {$PasswordAge = "<Not Set>"} $uac = $objuser.properties.item("useraccountcontrol") $uac = $uac.item(0) if (($uac -bor 0x0002) -eq $uac) {$disabled="TRUE"} else {$disabled = "FALSE"} if (($uac -bor 0x10000) -eq $uac) {$passwordneverexpires="TRUE"} else {$passwordNeverExpires = "FALSE"} } $record = "" | select-object SamAccountName,DistinguishedName,MemberOf,PasswordAge,LastLogon,LastLogonInDays,Disabled,PasswordNeverExpires,AccountExpires,Description,Notes $record.SamAccountName = [string]$sam $record.DistinguishedName = [string]$dn $record.MemberOf = [string]$parentGroup $record.PasswordAge = $PasswordAge $record.LastLogon = $lastLogon $record.LastLogonInDays = $lastLogonInDays $record.Disabled = $disabled $record.PasswordNeverExpires = $passwordNeverExpires $record.AccountExpires = $accountexpires $record.Description = $description $record.Notes = $notes }$record}####### Function to find all Privileged Groups in the Forest ##########Function getForestPrivGroups{ # Privileged Group Membership for the following groups: # - Enterprise Admins - SID: S-1-5-21root domain-519 # - Schema Admins - SID: S-1-5-21root domain-518 # - Domain Admins - SID: S-1-5-21domain-512 # - Cert Publishers - SID: S-1-5-21domain-517 # - Administrators - SID: S-1-5-32-544 # - Account Operators - SID: S-1-5-32-548 # - Server Operators - SID: S-1-5-32-549 # - Backup Operators - SID: S-1-5-32-551 # - Print Operators - SID: S-1-5-32-550 # Reference: http://support.microsoft.com/kb/243330 $colOfDNs = @() $Forest = [System.DirectoryServices.ActiveDirectory.forest]::getcurrentforest() $RootDomain = [string]($forest.rootdomain.name) $forestDomains = $forest.domains $colDomainNames = @() ForEach ($domain in $forestDomains) { $domainname = [string]($domain.name) $colDomainNames += $domainname } $ForestRootDN = FQDN2DN $RootDomain $colDomainDNs = @() ForEach ($domainname in $colDomainNames) { $domainDN = FQDN2DN $domainname $colDomainDNs += $domainDN } $GC = $forest.FindGlobalCatalog() $adobject = [adsi]"GC://$ForestRootDN" $RootDomainSid = New-Object System.Security.Principal.SecurityIdentifier($AdObject.objectSid[0], 0) $RootDomainSid = $RootDomainSid.toString() $colDASids = @() ForEach ($domainDN in $colDomainDNs) { $adobject = [adsi]"GC://$domainDN" $DomainSid = New-Object System.Security.Principal.SecurityIdentifier($AdObject.objectSid[0], 0) $DomainSid = $DomainSid.toString() $daSid = "$DomainSID-512" $colDASids += $daSid $cpSid = "$DomainSID-517" $colDASids += $cpSid } $colPrivGroups = @("S-1-5-32-544";"S-1-5-32-548";"S-1-5-32-549";"S-1-5-32-551";"S-1-5-32-550";"$rootDomainSid-519";"$rootDomainSid-518") $colPrivGroups += $colDASids $searcher = $gc.GetDirectorySearcher() ForEach($privGroup in $colPrivGroups) { $searcher.filter = "(objectSID=$privGroup)" $Results = $Searcher.FindAll() ForEach ($result in $Results) { $dn = $result.properties.distinguishedname $colOfDNs += $dn } }$colofDNs}########################## Function to Generate Domain DN from FQDN ########Function FQDN2DN{ Param ($domainFQDN) $colSplit = $domainFQDN.Split(".") $FQDNdepth = $colSplit.length $DomainDN = "" For ($i=0;$i -lt ($FQDNdepth);$i++) { If ($i -eq ($FQDNdepth - 1)) {$Separator=""} else {$Separator=","} [string]$DomainDN += "DC=" + $colSplit[$i] + $Separator } $DomainDN}########################## MAIN ############################ Get the script path$ScriptPath = {Split-Path $MyInvocation.ScriptName}$ReferenceFile = $(&$ScriptPath) + "\PrivilegedUsers.csv"$forestPrivGroups = GetForestPrivGroups$colAllPrivUsers = @()$rootdse=new-object directoryservices.directoryentry("LDAP://rootdse")Foreach ($privGroup in $forestPrivGroups){ Write-Host "" Write-Host "Enumerating $privGroup.." -foregroundColor yellow $uniqueMembers = @() $colOfMembersExpanded = @() $colofUniqueMembers = @() $members = getmemberexpanded $privGroup If ($members) { $uniqueMembers = $members | sort-object -unique $numberofUnique = ($uniqueMembers | measure-object).count Foreach ($uniqueMember in $uniqueMembers) { $objAttribs = getUserAccountAttribs $uniqueMember $privGroup $colOfuniqueMembers += $objAttribs } $colAllPrivUsers += $colOfUniqueMembers } Else {$numberofUnique = 0} If ($numberofUnique -gt $MaxUniqueMembers) { Write-host "...$privGroup has $numberofUnique unique members" -foregroundColor Red } Else { Write-host "...$privGroup has $numberofUnique unique members" -foregroundColor White } $pwdneverExpiresCount = 0 $pwdAgeCount = 0 ForEach($user in $colOfuniquemembers) { $i = 0 $userpwdAge = $user.pwdAge $userpwdneverExpires = $user.pWDneverExpires $userSAM = $user.SAM IF ($userpwdneverExpires -eq $True) { $pwdneverExpiresCount ++ $i ++ If ($DetailedConsoleOutput) {Write-host "......$userSAM has a password age of $userpwdage and the password is set to never expire" -foregroundColor Green} } If ($userpwdAge -gt $MaxPasswordAge) { $pwdAgeCount ++ If ($i -gt 0) { If ($DetailedConsoleOutput) {Write-host "......$userSAM has a password age of $userpwdage days" -foregroundColor Green} } } } If ($numberofUnique -gt 0) { Write-host "......There are $pwdneverExpiresCount accounts that have the password is set to never expire." -foregroundColor Green Write-host "......There are $pwdAgeCount accounts that have a password age greater than $MaxPasswordAge days." -foregroundColor Green }}write-host "`nComments:" -foregroundColor Yellowwrite-host " - If a privileged group contains more than $MaxUniqueMembers unique members, it's highlighted in red." -foregroundColor YellowIf ($DetailedConsoleOutput) { write-host " - The privileged user is listed if their password is set to never expire." -foregroundColor Yellow write-host " - The privileged user is listed if their password age is greater than $MaxPasswordAge days." -foregroundColor Yellow write-host " - Service accounts should not be privileged users in the domain." -foregroundColor Yellow}$colAllPrivUsers | Export-CSV -notype -path "$ReferenceFile" -Delimiter ';'# Remove the quotes(get-content "$ReferenceFile") |% {$_ -replace '"',""} | out-file "$ReferenceFile" -Fo -En ascii |
Enjoy!