Introducing the Sentinel LDK License Configuration Helper Service. This new tool I’ve created uses registry values and/or XML files to configure the client-side Sentinel LDK License Manager (hasplms) service, which updates the configuration in the License Manager Configuration File (hasplm.ini) found under the “C:\Program Files (x86)\Common Files\Aladdin Shared\HASP” folder on a 64-bit Windows machine. It achieves the same outcome as using the Configuration option from the Sentinel Admin Control Center (ACC) web interface via http://localhost:1947.
Background
Unlike Flexera’s FlexNet licensing, where you can simply push out the license server settings and changes via the registry using Group Policy, Sentinel HASP/LDK is missing the ability to this manage and configure it in the same way. This creates a challenge on the client-side when back-end license servers are migrated to new ones, or into the Cloud. Yes, you can create a job with tools like SCCM and Intune to update the hasplm.ini and restart the service (as recommended), but that’s not really the most efficient way.
A further challenge to this would be for those of us who use image management technologies, such as Citrix PVS or MCS, where you may need to update the underlying master image. It’s inefficient and a huge waste of peoples time and effort just to make a change to the remote license server list on every machine.
Some may create user instructions so users can configure via the Admin Control Center themselves, but that’s such a poor and lazy approach for the user experience. Again, if it’s non-persistent image based, these settings will be lost and users will need to complete this task each time they logon until a new base image has been rolled out.
Up till recently I’ve been using a computer startup script that configures the hasplm.in and restarts the service. But even using that method does not provide enough agility to make changes on the fly without a reboot.
Over time Thales did make it easier for Working Directly With License Manager Configuration Files without needing to restart the service. But I find their solution of “The easiest way to create a configuration file is to copy an existing file that was created using one of the License Manager tools and modify it to suit your requirements” lacks an understanding of enterprise level requirements.
The hasplm.ini file contains configuration information for the Admin License Manager. This file does not exist on a given machine until one or more configuration parameters in the Sentinel Admin API or Sentinel Admin Control Center have been modified for the first time on the machine.
Sentinel HASP was originally developed by Aladdin Knowledge Technologies, who SafeNet acquired in 2009. SafeNet was acquired by Gemalto in 2014. Gemalto was then acquired by Thales in 2019. If you follow the earlier development by Aladdin Knowledge Technologies, you will see it’s had a long life in the industry and is really one of four major license management solutions in use today, with Flexera’s FlexNet, Reprise License Management (RLM), and Wibu-Systems CodeMeter being the others.
A large majority of systems I deploy and manage have the Sentinel HASP/LDK Windows GUI Run-time Installer (HASPUserSetup.exe) deployed for licensing requirements of many application. So I wanted a way to achieve the same ease of management with Sentinel that we have with FlexNet, as it reduces a lot of complexity and makes a license change as quick as a Group Policy Refresh, which is up to 90 minutes across all machines without a reboot or service restart.
The Sentinel Admin Control Center web interface is added automatically when the HASP runtime or drivers are installed. I believe this web interface was introduced by SafeNet in circa 2009 from version 5.0 replacing the previous method of managing license servers via the Windows registry. Prior to this I understood that HASP license servers were managed using the “HKEY_LOCAL_MACHINE\SOFTWARE\Aladdin Knowledge Systems\HASP SRM\Server” registry key. It’s a real shame that they didn’t leave this level of management in place running alongside the Admin Control Center. It would of saved many headaches for many organizations over the years.
Thankfully in circa 2014 SafeNet released a version of the Sentinel LDK SDK, to align with the Sentinel LDK v6.0, which contained the AdminAPI Class. The Sentinel LDK SDK was specifically focused around application Vendors, enabling them to integrate the Sentinel licensing into their applications. The libraries they include are free for commercial use. The AdminApi Class allows you to programmatically control everything that relates to the Admin Control Center. There is .NET library they provide that I was able to use to create this Windows Service to achieve the outcome I was after. This provides an improved consistent automation for deployments and management instead of writing directly to the hasplm.ini and restarting the Sentinel LDK License Manager (hasplms) service, which is difficult to manage for licensing changes across the Enterprise.
The SafeNet “sntl_adminapi_net_windows.dll” .NET library is included as a reference within the tool. The “sntl_adminapi_windows_x64.dll” and “sntl_adminapi_windows.dll” C libraries are also included, as they are called by the “sntl_adminapi_windows_x64.dll” library. The current release of the project is 64-bit only. I’m happy to release a 32-bit version on request, but have not tested the code on 32-bit Windows to date.
For further information refer to the Sentinel documentation for the AdminApi Class.
Even with the AdminAPI .NET library, a majority of End User Computing (EUC), Infrastructure and Application IT Professionals most probably don’t have the coding skills needed, so won’t understand how to make use of this class. This is where I believe SafeNet/Gemalto/Thales have failed to enhance this further and provide improved examples, including PowerShell integration. It seems they have a narrow focus towards application Vendors only. In the end I decided that to achieve the outcome I wanted it needed to be coded in C# and run as a Windows Service. And if you know me, I love coding in C# 🙂
Whilst the primary reason for building this was to manage the license servers, I also added a mechanism to apply a base config when the service starts. An xml like file called BaseConfig.xml is included with this tool. It applies what I believe should be a base configuration on the client-side, as I don’t agree with some of the settings in the out of the box configuration from SafeNet/Gemalto/Thales. However, as it’s an XML file, you are free to make changes to this as you please.
Prerequisites
- .NET Framework 4.6.1 or greater must be installed.
- The Sentinel HASP/LDK Windows GUI Run-time Installer (HASPUserSetup.exe) must be installed.
Download and Installation Instructions
- Download the latest Release in the form of SentinelLDKLicenseConfigurationHelper.zip from Github. Total number of downloads to date: 59
- Create the “C:\Program Files\Sentinel LDK License Configuration Helper” folder.
- Extract the SentinelLDKLicenseConfigurationHelper.zip and copy the contents to the “C:\Program Files\Sentinel LDK License Configuration Helper” folder.
- If you have a license file, copy it to the “C:\Program Files\Sentinel LDK License Configuration Helper” folder. Note that the license file name can be whatever you want as long as it has a .lic file extension.
- Install the service using the following command line…
“C:\Program Files\Sentinel LDK License Configuration Helper\SentinelLDKLicenseConfigurationHelper.exe” install - From here you can open Windows Services Manager (services.msc) to verify that it is installed.
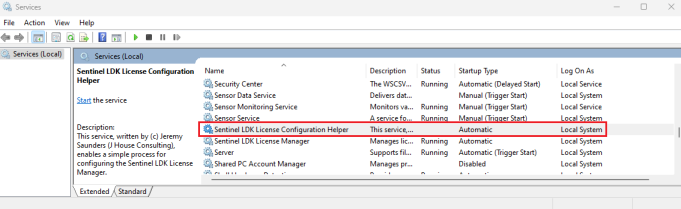 The service can be started from here , or it will automatically start after the next reboot reboot, or you can manually start it from the command line…
The service can be started from here , or it will automatically start after the next reboot reboot, or you can manually start it from the command line…
net start SentinelLDKLicenseConfigurationHelper - You can review the “C:\Program Files\Sentinel LDK License Configuration Helper\SentinelLDKLicenseConfigurationHelper.log” file at any time. You will only see basic information by default.
Configuration Details – AppSettings
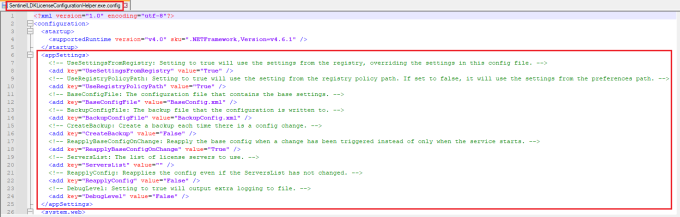
The SentinelLDKLicenseConfigurationHelper.exe.config contains the out of the box AppSettings. This can all be left as default, but I will run through each setting in more depth so you know what each one means.
- UseSettingsFromRegistry : default value is True
Setting to true will use the settings from the registry, overriding the settings in this config file, such as ServersList. - UseRegistryPolicyPath : default value is True
Setting to true will use the setting from the registry policy path. If set to false, it will use the settings from the preferences path.
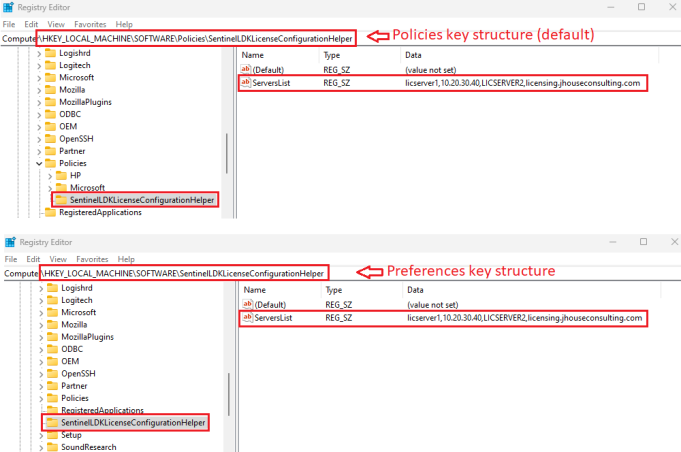
Registry Policy Path: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\SentinelLDKLicenseConfigurationHelper
Registry Preferences Path: HKEY_LOCAL_MACHINE\SOFTWARE\SentinelLDKLicenseConfigurationHelper - BaseConfigFile : default value is “BaseConfig.xml”, which is supplied with this tool.
The name of the configuration file that contains the base settings, which are always applied when the service is started and when there is a change detected in the ServersList values. - BackupConfigFile : default value is “BackupConfig.xml”
The name of the backup file that the configuration is written to before a change is made. - CreateBackup : default value is False
Setting this to True will create a backup each time there is a config change. I suggest leaving this set to False, as this is possibly an unnecessary step, but is here to be used if needed. - ReapplyBaseConfigOnChange : default value is True
This will ensure the base config is reapplied when a change has been triggered, instead of only when the service starts. This ensures the config returns to a consistent state in case users have made changes via the Admin Control Center over time. - ServersList : this is purposely left empty here, as it’s value is controlled via the registry or via an XML file.
A comma separated list of remote license servers can be added to the configuration if needed here. - ReapplyConfig : default value is False
Setting this to True will reapply the config even if the ServersList has not changed. I suggest leaving this set to false, or the config will be reapplied on every Group Policy Refresh if the GPP registry action is set to replace, even if the ServerList has not changed. This is because the “replace” action will first delete and then recreate the value, which will trigger the registry watcher method in this service unnecessarily. - DebugLevel : default value is False
Setting to True will output verbose logging to the SentinelLDKLicenseConfigurationHelper.log file, which is extensive. I suggest setting this to True during testing only, which will help you understand how the service works. Make sure it’s left set to False when deployed in production.
Configuration Details – BaseConfigFile
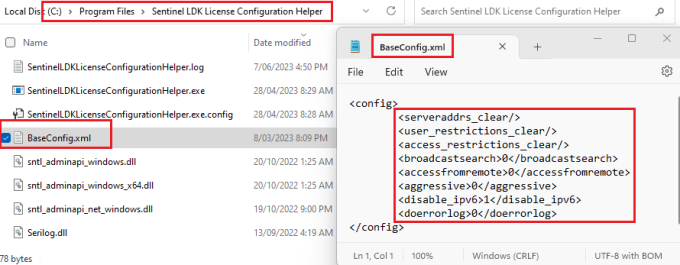
The base config file supplied with the service will configure the settings each when the service starts.
- serveraddrs_clear : This will clear the remote license servers list.
- user_restrictions_clear : This will clear any user restrictions.
- access_restrictions_clear : This will clear access restrictions.
- broadcastsearch : Setting it to 0 disables a broadcast search for remote Sentinel License Managers on the local network. This reduces noise (network traffic) as the Sentinel License Managers would rarely ever exist on the same local network as the client machines.
- accessfromremote : Setting it to 0 prevents remote machines from accessing the local Sentinel License Manager. Client machines should not be communicating with each other. They should only be communicating with remote Sentinel License Managers.
- aggressive : In my experience setting this to 0 reduces the network traffic. However, for run-time Environment version 8.3.1 and later, this parameter is always assigned the value 1 regardless of the value specified. I’ve left this here for older run-time versions.
- disable_ipv6 : Setting this to 1 disables the IPv6 protocol.
- doerrorlog : Setting this to 0 disables logging of errors. This is done to reduce noise from log files. If you have an issue you want to debug, you can enable the logging on a handful of machines.
To understand more about the makeup of these XML files, please refer to the Changing Configuration Settings for Sentinel License Manager documentation.
Configuration Details – Registry
With the UseSettingsFromRegistry value set to True, some of the settings can be set in the registry, which will override the settings in the AppSettings section of the SentinelLDKLicenseConfigurationHelper.exe.config file. However, the main setting we want to manage this way is the ServersList.
If the UseRegistryPolicyPath value is set to True, it will use the Policies key structure. If it’s set to False, it will use the Preferences key structure.
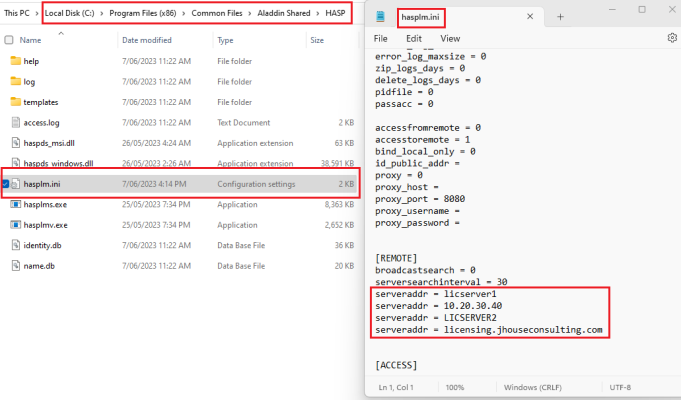
The ServersList value is a comma separated string. The example screen shot below shows that you can use lowercase hostnames, uppercase hostnames, IP Addresses, and fully qualified domain names (FQDNs).
If a change is detected by the registry watcher method of the service, it will pause for 10 seconds, and then process the change. The 10 second pause prevents multiple triggers being generated from a Group Policy Refresh.
Configuration Details – Files
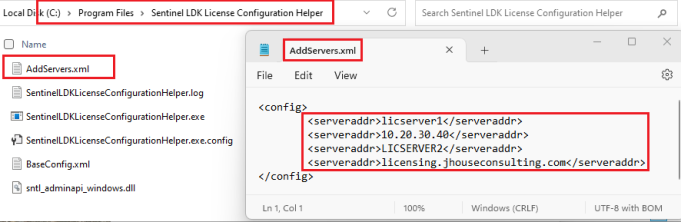
If UseSettingsFromRegistry value set to False, you can deploy XML style config files that will be detected by a file watcher method of the service and processed.
Here’s an example of an XML file. We just wrap a list of serveraddr elements in config tags.
You can deploy multiple files. It will process them all in alphabetical order.
XML files with the following names are not processed by the file watcher:
- A name that matches SentinelLDKLicenseConfigurationHelper.xml
- A name that matches the BaseConfigFile, such as BaseConfig.xml
- A name that matches the BackupConfigFile , such as BackupConfig.xml
- A name that contains Microsoft*.xml, as it’s part of a reference library used.
- A name that contains Serilog*.xml, as it’s part of a reference library used.
- A name that matches Topshelf.xml, as it’s part of a reference library used.
Logging
Logging is written to the SentinelLDKLicenseConfigurationHelper.log file.
With DebugLevel set to False, it will only write out basic information. Setting it to True will output verbose logging to the log file, which is extensive. I suggest setting this to True during testing only, which will help you understand how the service works. Make sure it’s left set to False when deployed in production.
Licensing
Whist you can test this tool, and request a 30 day trial license, it is not free. Please contact me via e-mail (jeremy@jhouseconsulting.com) to request a trial license and pricing.
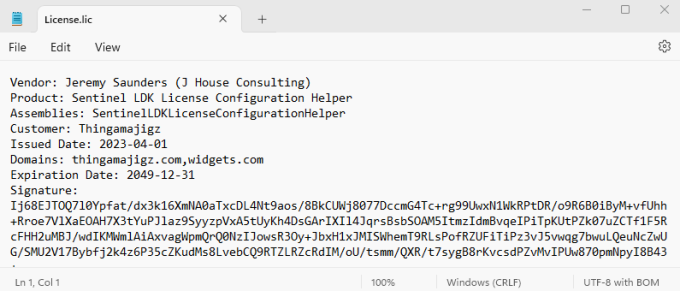
When you receive a license file, it may look like the following screen shot.
The service is licensed based on domain membership of the computer it’s run on. I can add multiple domains to the list. If you have a Forest domain where child domain names are are part of the same contiguous namespace, then licensing it based on the the Forest domain name will automatically include licensing for all child domains.
Any changes to the license file will render it invalid.
When the service starts it will check all .lic files for a valid license. If the license cannot be verified, the service will continue to run for 10 minutes before clearing the remote license servers list, user restrictions, and access restrictions, and then stopping itself. This provides more than enough time to test the basic functionality and purpose of the tool. Further to this, if the license is not valid when the service starts, it will clear the config in the same way if the service is stopped under normal conditions. This is done purposely to prevent people from starting and stopping the service on a schedule in an attempt to apply the config and work around the licensing mechanism.
The published project has been obfuscated to protect my intellectual property. Obfuscation prevents decompiling, reverse engineering, and then duplication of this project.
Outcome
Once setup and configured the service will take care of the rest.
To verify that it’s applied, you can check the hasplm.ini as per the following screen shot.
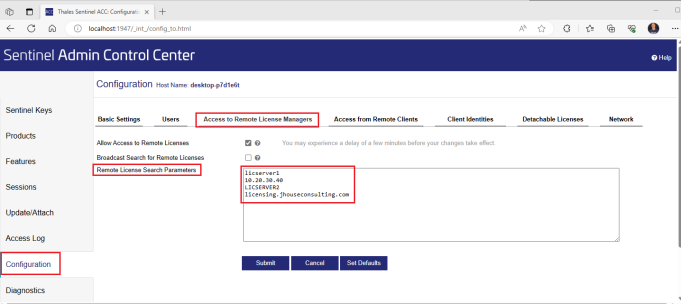
You can also check the Remote License Search Parameters list under the Configuration option from the Sentinel Admin Control Center (ACC) web interface via http://localhost:1947 as per the following screen shot.
A final test would be to start an application on the client that leverages Sentinel licensing and ensure it acquires a license.
Uninstallation Instructions
- Stop the Service by typing…
net stop SentinelLDKLicenseConfigurationHelper - Uninstall the service using the following command line…
“C:\Program Files\Sentinel LDK License Configuration Helper\SentinelLDKLicenseConfigurationHelper.exe” uninstall - Delete the “C:\Program Files\Sentinel LDK License Configuration Helper” folder.
- Delete the the registry structure.
Final Words
I only started working on this project on 26th January 2023 in my own time outside of business hours and completed it by 28th April 2023. I wished I have of got cracking on this years ago, as it would of saved me and the teams I work in many headaches.
Please reach out for more information, any questions you have, or any enhancements you would like to see.
Thanks,
Jeremy